Firewall Rules FAQ
General
How many rules can I have on my site?
You can create a large number of rules. However, the number of active rules at any given time is limited. Refer to Availability for details on what is allowed per customer plan.
Can I purchase additional active rules?
No. The number of active rules is fixed based on customer plan. Refer to Availability.
Why does a firewall event display a Cloudflare IP address even though other fields match the client details?
This happens when a request goes through a Cloudflare Worker.
In this case, Cloudflare considers the client details, including its IP address, for triggering security settings. However, the IP displayed in Security Events will be a Cloudflare IP address.
Rule configuration
How are certain special and escaped characters handled?
When used as literals in an expression, the backslash \ and double quote " characters require proper escaping.
An expression built using the visual Expression Editor does not require you to manually escape those special characters. Conveniently, the Expression Builder takes care of any necessary escaping in the final expression by automatically prepending a backslash such that \ and " become \\ and \", respectively.
The following image illustrates how double quotes are automatically escaped to \" once they appear in the plain text expression generated in the Expression Editor:
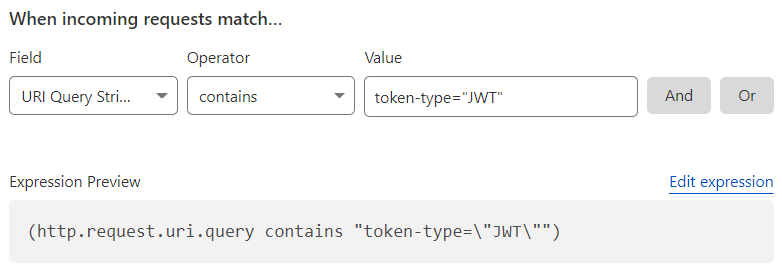
Why isn’t my regular expression pattern matching working?
If you are using a regular expression, it is recommended that you test it with a tool like Regular Expressions 101 or Rustexp.
Also, note that the http.request.method field requires all-caps for method names (for example, POST).
How can I use the Threat Score effectively?
The Cloudflare Threat Score is a key item behind the Security Level functionality in the Cloudflare dashboard.
Threat Score as configured by Security Level is based on:
- High - for scores greater than 0
- Medium - for scores greater than 14
- Low - for scores greater than 24
- Essentially off - for scores greater than 49
Enabling a high threat score for sensitive areas - like comment form pages or login forms - can add an effective level of protection. Integrating Threat Score with firewall rules is advantageous because you can specify an Interactive Challenge vs. a JS Challenge, or even a block. You can also exclude IP addresses using and not logic.
How do I create an exception to exclude certain requests from being blocked or challenged?
There may be situations in which you want to enforce a blocking or challenging action but make exceptions for specific types of requests.
Cloudflare supports two methods to allow requests through firewall rules expressions:
- Exclude a type of request from being blocked or challenged, for example based on IP address, ASN, or country.
- Create an independent firewall rule with an Allow action.
If you wish to permit certain exclusions, the examples below illustrate a few possible approaches.
Example 1
Exclude multiple IP addresses from a blocking/challenging rule that assesses Threat Score.
| Basic rule, with no exclusion | |
| Action | Block (or a challenge action) |
| Expression |
(http.host eq "example.com" and cf.threat_score > 5)
|
| Rule that excludes IP addresses from being blocked/challenged | |
| Action | Block (or a challenge action) |
| Expression |
(http.host eq "example.com" and cf.threat_score > 5) and not (ip.src in
{192.0.2.1 198.51.100.42 203.0.113.0/24})
|
| Two rules to allow exceptions and block the rest | |
| Rule 1 |
Action: Allow
Expression: ip.src in {192.0.2.1 198.51.100.42 203.0.113.0/24}
|
| Rule 2 |
Action: Block (or a challenge action)
(http.host eq "example.com" and cf.threat_score > 5)
|
Example 2
Block Amazon Web Services (AWS) and Google Cloud Platform (GCP) because of large volumes of undesired traffic, but allow Googlebot and other known bots that Cloudflare validates.
| Basic rule, with no exclusion | |
| Action | Block (or a challenge action) |
| Expression | (ip.geoip.asnum in {16509 15169}) |
| Rule that excludes known bots that Cloudflare validates | |
| Action | Block (or a challenge action) |
| Expression |
(ip.geoip.asnum in {16509 15169} and not cf.client.bot)
|
| Two rules to allow exceptions and block the rest | |
| Rule 1 |
Action: Allow Expression: cf.client.bot
|
| Rule 2 |
Action: Block (or a challenge action) Expression: (ip.geoip.asnum in {16509 15169})
|
Bots
How does Firewall Rules handle traffic from known bots?
Caution about potentially blocking bots
When you create a firewall rule with a Block, Interactive Challenge, JS Challenge, or Managed Challenge (Recommended) action, you might unintentionally block traffic from known bots. Specifically, this might affect search engine optimization (SEO) and website monitoring when trying to enforce a mitigation action based on URI, path, host, ASN, or country.
Refer to How do I create an exception to exclude certain requests from being blocked or challenged?.
Bots currently detected
Cloudflare Radar lists a sample of known bots that Cloudflare Firewall Rules currently detects. When traffic comes from these bots and others not listed, the cf.client.bot field is set to true.
If you need to submit a friendly bot to be verified, use our online form.
Challenges
Do the Challenge actions support content types other than HTML (for example, AJAX or XHR requests)?
No. The Managed Challenge, Interactive Challenge, and JS Challenge actions only support requests that trigger a page refresh.
Challenges presented to users display an intermediate page where they must prove they are not a bot. This concept does not work over XHR or AJAX, such as in Single Page Applications (SPA), since visitors do not trigger a new page load.
When an XHR or AJAX request triggers a Challenge action, the HTTP response will have a 403 status code.
Your application can use this status codes to handle unexpected challenges, optionally using a Custom Error Response for XHR and AJAX requests instead of a Challenge action. The application could capture the custom error response and raise a challenge by, for example, triggering a page refresh.
For an additional layer of security against Credential Stuffing, you could use Cloudflare Turnstile on the most vulnerable parts of your site (such as login or checkout forms).
Does the ‘challengeFailed’ action accurately represent challenges that users did not pass?
No. The challengeFailed and jschallengeFailed firewall rule actions account for observed requests that, under special circumstances, did not pass a challenge. However, some failed challenges cannot be traced back to a firewall rule. Additionally, Cloudflare Firewall Rules may not have a record of every request with a failed challenge.
Therefore, consider these actions with caution. A reliable indicator is the Challenge Solve Rate (CSR) displayed in Security > WAF > Firewall rules, which is calculated as follows: number of challenges solved / number of challenges issued.
Why would I not find any failed challenges? Why is ‘ChallengeIssued’ not equal to ‘ChallengeSolved’ plus ‘ChallengeFailed’?
Users do not complete all challenges. Cloudflare issues challenges that are never answered — only 2-3% of all served challenges are usually answered.
There are multiple reasons for this:
- Users give up on a challenge.
- Users try to solve a challenge but cannot provide an answer.
- Users keep refreshing the challenge, but never submit an answer.
- Cloudflare receives a malformed challenge answer.
Why do I have matches for a firewall rule that was not supposed to match the request?
Make sure you are looking at the correct request.
Only requests that triggered a challenge will match the request parameters of the rule. Subsequent requests with a [js]challengeSolved or [js]challengeFailed action may not match the parameters of the rule — for example, the bot score may have changed because the user solved a challenge.
The “solved” and “failed” actions are informative actions about a previous request that matched a rule. These actions state that “previously a rule had matched a request with the action set to Interactive Challenge or JS Challenge and now that challenge was answered.”