strongSwan
This tutorial explains how to set up strongSwan along with Magic WAN. You will learn how to configure strongSwan, configure an IPsec tunnel and create a Policy Based Routing.
1. Health checks configuration
Start by configuring the symmetric health checks target for Magic WAN as explained in tunnel health checks. For this particular tutorial, we are using 172.64.240.252 as the target IP address, and type as the request.
This can be set up with the API. For example:
2. Configure StrongSwan
- Start by installing StrongSwan. For example, open the console and run:
- After StrongSwan finishes installing, go to
/etc/strongswan.confto edit the configuration file and add the following settings:
3. Configure IPsec file
- Go to
/etc/ipsec.confand add the following settings:
-
Now, you need to create a virtual tunnel interface (VTI) with the IP we configured earlier as the target for Cloudflare’s health checks (
172.64.240.252) to route IPsec packets. Go to/etc/strongswan.d/ -
Create a script called
ipsec-vti.shand add the following:
4. Add Policy Based Routing (PBR)
Although the IPsec tunnel is working as is, we need to create Policy Based Routing (PBR) to redirect returning traffic via the IPsec tunnel. Without it, the ICMP replies to the health probes sent by Cloudflare will be returned via the Internet, instead of the same IPsec tunnel. This is required to avoid any potential issues.
To accomplish this, the tutorial uses
iproute2 to route IP packets from 172.63.240.252 to the tunnel interface.
-
Go to
/etc/iproute2/. -
Edit the
rt_tablesfile to add a routing table number and name. In this example, we usedviatunicmpas the name and200as the number for the routing table.
- Open the console and add a rule to match the routing table just created. This rule instructs the system to use routing table
viatunicmpif the packet’s source address is172.64.240.252:
- Add a route to the newly created routing table
viatunicmp. This is the default route via the interfacevti0in theviatunicmptable.
- Now, you can
startIPsec. You can alsostop,restartand show thestatusfor the IPsec connection:
5. Check connection status
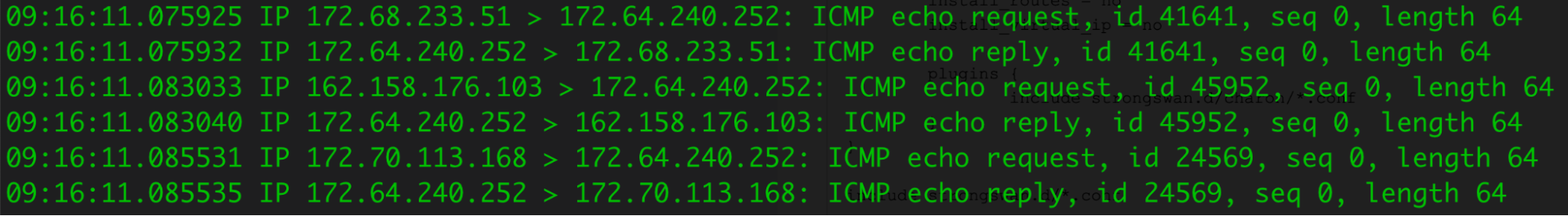
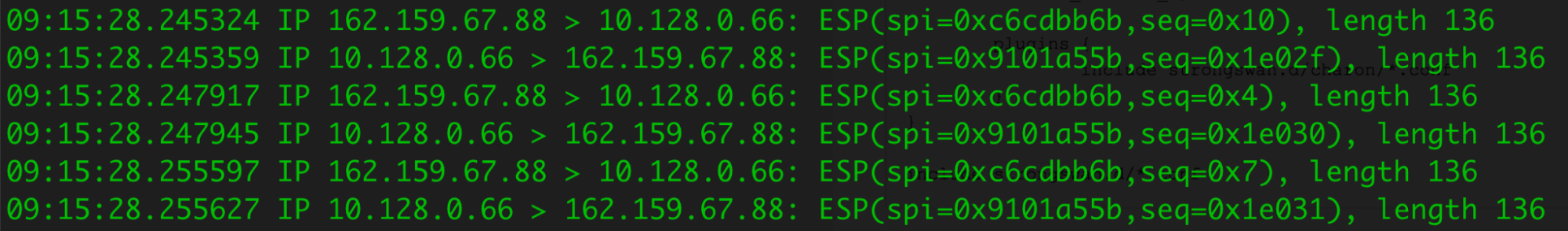
After you finish configuring StrongSwan with Magic WAN, you can use tcpdump to investigate the status of health checks originated from Cloudflare.
In this example, the outgoing Internet interface shows that the IPsec encrypted packets (ESP) from Cloudflare’s health check probes (both the request and response) are going through the IPsec tunnel we configured.
You can also run tcpdump on vti0 to check the decrypted packets.