Add a self-hosted application
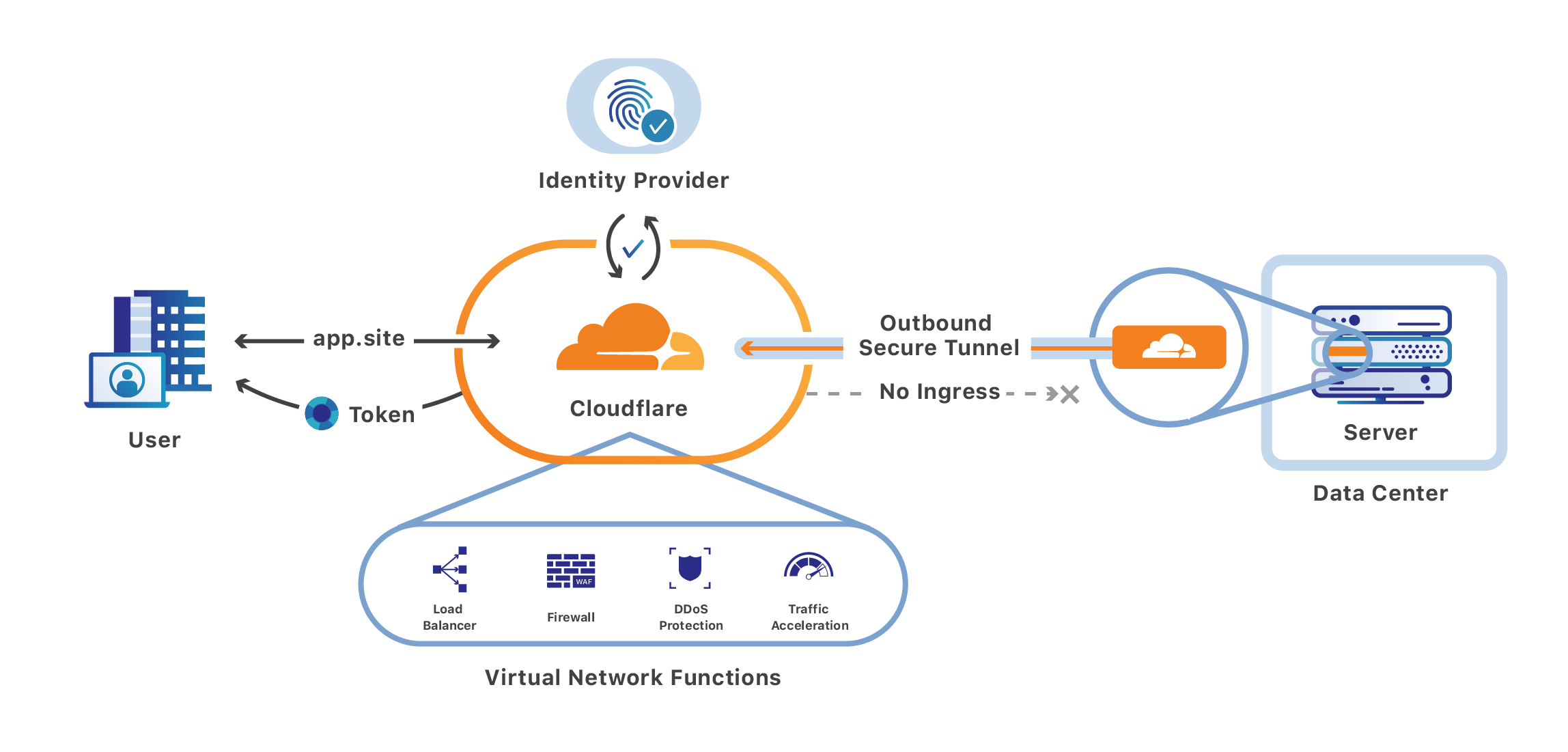
Cloudflare Access allows you to securely publish internal tools and applications to the Internet by providing an authentication layer between the end user and your origin. You can use signals from your existing identity providers (IdPs), device posture providers, and other rules to control who can access your application.
Prerequisites
- Add your domain to Cloudflare.
- Change your domain nameservers to Cloudflare, or configure a partial (
CNAME) setup.
1. Add your application to Access
-
In Zero Trust, go to Access > Applications.
-
Select Add an application.
-
Select Self-hosted.
-
Enter any name for the application.
-
Choose a Session Duration. The session duration determines the minimum frequency for which a user will be prompted to authenticate with the configured IdP. If you want users to re-authenticate every time they reach your application, select No duration, expires immediately.
-
In Application domain, enter the domains that will represent the application.
- Domains must belong to an active zone in your Cloudflare account. You can either select a domain from the dropdown or enter a custom domain that you control.
- You can use wildcards to protect multiple parts of an application that share a root path.
-
(Optional) Under Application Appearance, configure App Launcher settings for the application.
-
Under Block pages, choose what end users will see when they are denied access to the application:
- Cloudflare default: Reload the login page and display a block message below the Cloudflare Access logo. The default message is
That account does not have access, or you can enter a custom message. - Redirect URL: Redirect to the specified website.
- Custom page template: Display a custom block page hosted in Zero Trust.
- Cloudflare default: Reload the login page and display a block message below the Cloudflare Access logo. The default message is
-
In the Identity Providers card, select the identity providers you want to enable for your app.
-
(Optional) Turn on Instant Auth if you selected only one IdP and want users to skip the identity provider selection step.
-
Select Next.
2. Add an Access policy
You can now configure an Access policy to control who can connect to your application.
-
Enter any name for your rule.
-
Specify a policy action.
-
Assign Access groups to reuse existing rules, or create new rules. You can add as many include, exception, or require statements as needed.
-
(Optional) Customize the login experience for users who match this policy:
-
Select Next.
3. (Optional) Configure advanced settings
You can configure the following advanced settings for your application:
- Cross-Origin Resource Sharing (CORS)
- Cookie settings
- Automatic
cloudflaredauthentication - Browser rendering
To finish configuring the application, select Add application.
4. Connect your origin to Cloudflare
Next, set up a Cloudflare Tunnel to make your internal application available over the Internet.
5. Validate the Access token
To secure your origin, you must validate the application token issued by Cloudflare Access.
One option is to configure the Cloudflare Tunnel daemon, cloudflared, to validate the token on your behalf. This is done by enabling Protect with Access in your Cloudflare Tunnel settings. If you do not wish to use Cloudflare Tunnel, you can manually configure your origin to check all requests for a valid token.
Users can now connect to your self-hosted application after authenticating with Cloudflare Access.
Product compatibility
When using Access self-hosted applications, the majority of Cloudflare products will be compatible with your application.
However, the following products are not supported:
If these products are enabled for your Access application, disable them using a Configuration Rule scoped to the application domain.